Is Your Security a 737 Max 9?
As you may know, a door blew off a flight mid-air minutes after takeoff at 16,000 feet forcing an emergency landing. Thankfully and miraculously no loss of life occurred, but it could have been really, really bad. I think someone did lose a cell phone.
Systemic Failures In History
This is an example of a systemic failure all around, that is not exclusive to the aviation field, despite it being one of the most regulated environments existing.
Let’s try to recall some similar systemic failures:
Enron
2007- 2008 Financial Crisis
2014 Target Breach
2017 Equifax Breach
Boeing Failures vs Cybersecurity Failures
Back to Boeing, there is a lot of blame to go around, but let’s look at some of the information we have:
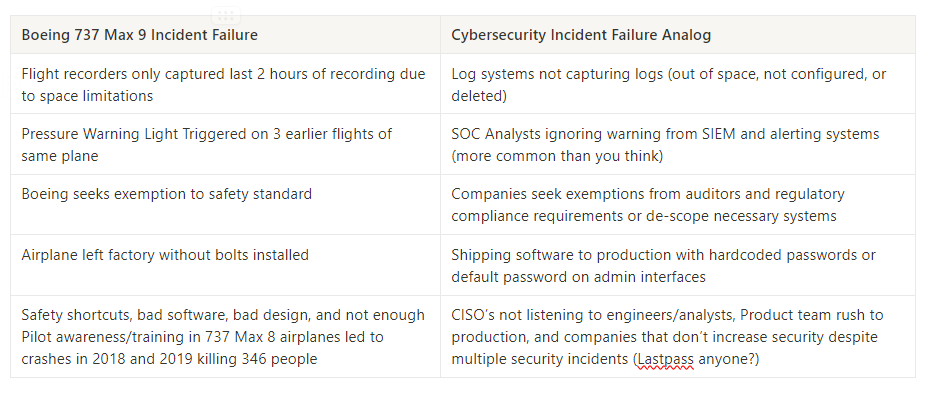
Boeing Failures vs Cybersecurity Failures
Do you have a gaping hole in your security? Have some unknown unknowns? Schedule an assessment today
Success Factors From Failures We Can Learn
Failures happen. It’s a fact of life. My son looks at me when he’s spilled milk, and I tell him it’s ok, you didn’t do it on purpose right, it’s just an accident.
It is only a loss if we can’t learn from our failures.
Some factors to consider from the Boeing Incident:
The plane was banned from long distance ocean travel (what a disaster that would have been!)
All 737 Max 9 jets were grounded by the FAA (we don’t have an FAA in cybersecurity)
Complacency may take a rest, for now (only because it affects their bottom line)
Cybersecurity Takeaways
The same thing happens after a security incident. Many companies are reactive in nature and although many decide to reflect and improve themselves, sometimes it takes a couple incidents for them to get their act together.
Here is a quick list of concepts you can takeaway and implement at your org today for better security:
Trust, But Verify
We first had this wakeup call during Operation Aurora when Google and many other’s IP was stolen by an embedded and foreign adversary. Back then it was OK to not encrypt connections within the datacenter.
Assume Breach
Design your systems to prevent adversaries within your system to steal or alter data.
Auditors and Analysts Are Still Humans
Have an audit report from a company. Read it. Understand what you’re looking at. Know what questions to ask and feel free to ask the same questions again from the company. This goes back to Trust But Verify.
Analaysts are human too. Sometimes they get complacent. It’s a natural human tendency. Rotate staff so that they’re exposed to other environments and bring fresh perspectives.
Build Backups and Backups to Backups
Be creative on what could go wrong. Have fun with it, but come back of course to reality. Take into consideration various What If scenarios, and actually prepare for those moments. Conduct tabletop exercises often and test your systems thoroughly.
Thanks so much for reading! Have a great rest of your week!